
LOW CURRENT
SECURITY
CCTV Remote Surveillance Solutions.
• Analytics Camera
• LPR Camera
• Video Management Systems
• Video Walls
• Thermal Camera
• UVIS ‘Under Vehicle Inspection Systems’
• City Surveillance
• Facial Recognition Systems
Detection and Protection Systems.
• Intrusion Detection Systems
• Perimeter Protection
• Panic System
• Electronic article surveillance (EAS)
• Guard Tour System
• Explosive Detectors
• Metal Detectors
• Screening Machines
• Pipeline Protection
HRMS Security Solutions.
• Access Control
• Time Attendance Integration
• HRMS
Additionally:
• Barrier Security Solutions
• Facility Management Systems
• Audio Visual Solutions

CCTV Remote Surveillance Solutions
In the modern era, it is imperative to take security seriously. Not just enterprises and commercial buildings, but also our residences require effective security. Given the rise in crime and the frequency of burglaries, it is crucial to weigh your security alternatives and select the one that is best for you.
Using CCTV cameras and equipment is one of the most common and economical ways to provide security in the home and place of employment. CCTV equipment can work as an extremely effective deterrent to thieves and robbers, making them at least think twice. Modern security equipment is made with highly sophisticated technology. In recent years, companies have understood the value of including video surveillance in their operations plans. Observe your surroundings, look for movement, and simultaneously capture video from a number of remote cameras. For the best security, use these remote cameras as your second set of eyes. To guarantee that the system’s design results in an installation that appropriately handles the threats and lowers the security risks, a threat, vulnerability, and risk assessment should be carried out. The amount of detail needed in an image must be taken into account so that it meets the user’s needs. (Monitor, identify, detect, observe, confirm, and inspect).
The environment should also be taken into account by the designer. Therefore, the design should be created by experts, and this is where we come in.
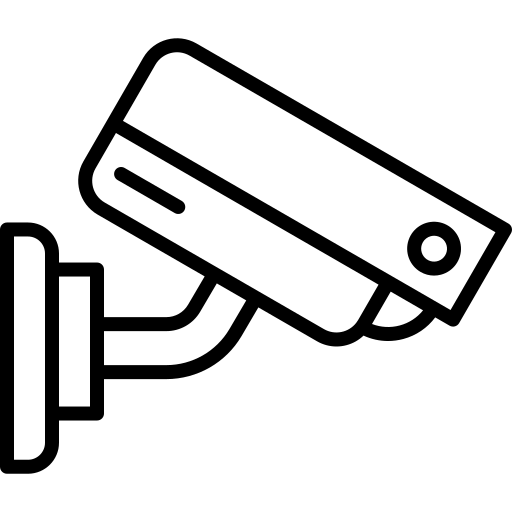
CCTV Remote Surveillance Solutions

Analytics Camera
Analytics algorithms work around-the-clock, 365 days a year, without becoming bored or losing interest, and they have a major positive impact on both live-monitored and incident review operations. Their use enables a monitoring and control institution to adapt higher operational performance and an increased workload without adding more staff members. This device offers larger coverage with an immediate warning solution without the infrastructure costs associated with conventional intrusion and surveillance systems.

LPR Camera
The License Plate Reader (LPR) System adds a new level of information for making decisions on security and traffic control. It employs a distinctive, patented method that automatically identifies the existence of any vehicle in its field of view, takes a picture of the license plate, finds the car, and reads the plate number and state of origin. All varieties of license plates—retroreflective, non-retroreflective, embossed, flat, and others—can be read by the LPR. The LPR uses real-time processing after capturing the license plate to reduce transit and waiting times

Video Management Systems
Security management teams and the raw data from camera inputs and storage bins are connected by video management systems. To make your operations simpler, EJAD uses the most recent VMS solutions and unified security platform, which seamlessly combines IP security surveillance equipment into a single userfriendly interface.

Video Walls
For dynamic digital signage and informational video wall applications, EJAD offers high quality commercial and professional grade digital video wall solutions. Exclusive technologies enable easy installation and brilliant, astounding video walls when paired with LED backlighting, high-definition quality, and the ultranarrow bezels.

Detection and Protection Systems

Intrusion Detection
Increased procedures and countermeasures to prevent or detect an intrusion greatly improve a security system. This entails using a number of security areas that are either manually or automatically monitored. EJAD offers a full line of intrusion detection systems (IDS), that help increase the effectiveness of the on-site security resources by preventing, detecting, and delaying the entry of unauthorized people and vehicles into a facility. In order to function in a specific way, IDS are primarily made up of sensors, video camera detection, control units, and data communications systems.

Perimeter Protection
Outdoor perimeter protection sensors catch attackers the moment a protected area is accessed, preventing them from accessing people or valuable assets or property. Their use, along with video surveillance systems, adds a core and fundamental layer of protection by keeping an eye on shady actions close to perimeter borders, which enables specialized operators to implement the appropriate security measures in response. Outdoor perimeter protection systems activate the security measures that follow, including the CCTV cameras.

Panic Systems
The panic system offered by EJAD is utilized as a simple call for assistance. Panic buttons offer significant alerting capabilities for various crucial conditions, even though they are primarily employed in Intrusion Detection Systems for Hold-up alarm applications. Panic buttons come in wired and wireless varieties.

EAS
EJAD offers a range of electronic article surveillance (EAS), a technical technique, can stop theft from stores. Products are fixed with unique tags. When the item is correctly purchased or checked out, the clerks remove or deactivate these tags. When a detection system detects active tags at the store’s exits, it sounds an alarm or otherwise notifies the employees.
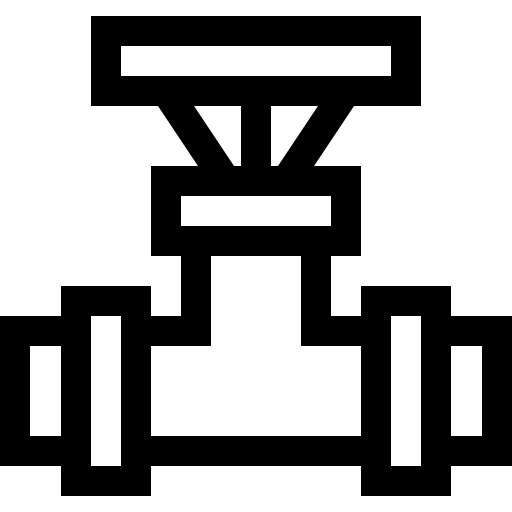
Pipeline Protection Systems

Pipeline Protection and Leak Detection Systems
Innovative pipeline protection strategies that ensure quick incident detection, categorization, localization, and threat response help prevent third party interference. The longer it takes to notice and fix a pipeline leak caused by a security breach, the more severe the environmental and financial effects would be. Sometimes it takes pipeline workers days to pinpoint the exact location of the leak.
Traditional observational patrols are ineffective in keeping watch over the hundreds of kilometers of pipeline that are frequently present in normal national or cross-border pipeline infrastructure, despite being effective in the nearby area.
In order to provide early warning, deterrent, and denial of threats that affect onshore and offshore pipeline security & safety, EJAD offers pipeline operators customized combinations of physical and technological security solutions.
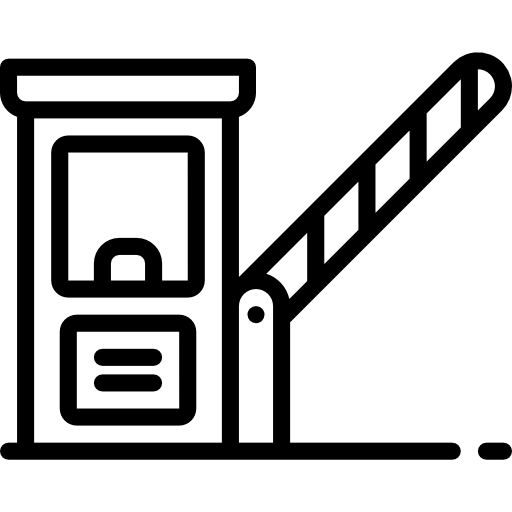
Barrier Security Solutions

Barriers
The most effective way to manage car traffic at any facility is using swinging parking barrier gates since they are affordable and practical. Our entry-level barrier arm gate is reasonably priced, works without a hitch, and comes in the exact length you need. These gates offer a low-cost solution to access management in numerous circumstances, such as parking lots and parking ramps, from industrial settings and government buildings to residential and recreational sites.

Road Blockers and Tyre Killers
Road blockers are specifically made for entrances that could be attacked by vehicles or that need to meet strict security standards. One of the most secure vehicle access control systems is Mechanical Tire-Killer. For critical locations (banks, military bases, airports, embassies, etc.), The Tire-Killer offers exceptional protection against forcible and unlawful entry or leave of motor vehicles.

Turnstile and Sliding Gates
Many organizations place a high priority on managing access to buildings, land, and specific zones. A range of forms and designs are needed to accommodate all access control requirements. Turnstiles and turnstile security gates of all varieties are a crucial class of access control equipment. You may get the help and guidance you need from our turnstile specialists to choose the right goods.

Bollards
EJAD offers a range of electronic article surveillance (EAS), a technical technique, can stop theft from stores. Products are fixed with unique tags. When the item is correctly purchased or checked out, the clerks remove or deactivate these tags. When a detection system detects active tags at the store’s exits, it sounds an alarm or otherwise notifies the employees.

Audio and Visual Solutions

PABX
(Private Automatic Branch Exchange)
EJAD offers a PABX system, a fantastic choice for bigger enterprises with lots of employees, including call centers. In essence, it is a scaled-down replica of company’s central switching phone.

Public Address Systems
A public address system is an electronic sound amplification and distribution system that includes a microphone, amplifier, and loudspeakers and is used to enable a person to address a large audience, for example, to announce movements at busy and large airport and rail terminals or at sporting events. This equipment may also include a mixing console, amplifiers, and loudspeakers suitable for both music and speech.

Audio Video Intercoms
A high quality monitor, a wide angle camera to record a wider area, LED lighting to view at night, and of course the voice intercom itself are all included in the video intercom systems that EJAD offers.

Audio Visual and Media
To identify the finest audiovisual solution for your project, we help evaluate your needs. We offer everything from sound systems for auditoriums to paging and background music systems.

People Counting System
Our sensors, which use thermal technology to count persons who pass underneath, can be installed outside in weather-resistant housings or discretely into the ceiling of your building. Even in busy areas, you can count individuals precisely thanks to our powerful algorithms. Data can be accessed remotely over an internet connection using either your own application or our estate management and data gathering tool. Additionally, you can network various sensors, segmenting areas as necessary to assess their effectiveness at any degree of detail you choose.









